Fortigate IPsec Tunneling between Sites on EVE-NG Lab
- hamidullahbayram
- 1 Haz 2023
- 2 dakikada okunur
How to secure remote access to an enterprise network system? Demand for reliable and secure virtual networks is growing day by day. One of most common VPN tunneling is Internet Protocol Security (IPsec) for secure network traffic, yet the speed is not a choice, but the requirement. It provides encrypted network data and operates at Layer3, so the sent data identified by IP addresses between the systems. It enables remote connection between host to entire networks and is mostly used for IP-based applications. It is less secure against SSL while the connection is specified and attack surface restricted, since the gateway location is deployed behind the firewall on SSL-VPNs unlike it is implemented on the firewall for IPsec. This article is more about how to set up IPsec on Eve-NG lab environment beyond what is IPsec.
Here is my topology below and is needed remote access between the sites. Configurations for Firewall and Switches (trunk mode etc.) have been done as well as policies on firewall have already been created on both sides. In this scenario, I will try to reach WinServer at Site-B on the 2nd floor from my Win7 machine at Site-A on the 1st floor under the Management Vlan.

To do this, we should create IPsec Tunnel in the firewalls on both sides, that have the same configuration. Let’s start with firewall Site-A.
> Go to IPsec Tunnels feature under the VPN tab on Fortigate admin menu, and click on the Create new on right side.

> Set a name for remote access

> Chose Static IP address and set the IP address of remote access point (Site-B_Fw), then chose the WAN as access port.

> Determine a pre-shared key which will be used the same key on the other site, set the encryption method for the outgoing traffic. Leave the rest as it is.

> Continue with Phase2 deciding the permission for networks access between the sites, either you can add a specific subnets. I chose that whole connecction is up between all networks. Then again set the encryption method for incoing traffic. You can click the "Auto-negotiate" box lest the system is down while no one uses.

> Then save it, my Ipsec configuration is done on Site-A_Fw.

> but not finish with Site-A, create Static Route under the Nertwork tab for vlans so that they can communicate each other. Then create Ipsec-Zone on Interfaces feature to be added within a policy for accepted access between sites.




> Continue the same configuration on Site-B_Fw. For this time, set the Site-A's IP address for remote access.


> again Static Routes, Zone interfaces, and Policies...


> Now my IPsec-VPN is up...

> It is time to check whether connection is ready... machines get IP adresses from the DHCP server (related interface in Firewall has been cinfigured as dhcp). They can ping to each other too.


> Now I can try RDP connection to the Windows Server16 from my Win7 machine on the Central Site (SIte-A).
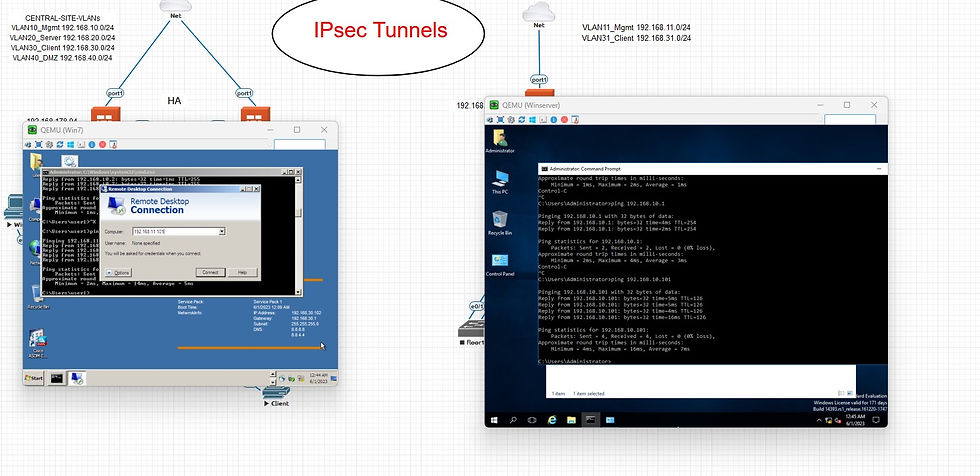

> I've got the connection and WinServer16 screen via RDP...

Yorumlar